If you've ever dived into memory corruption vulnerabilities or exploit development, you've probably stumbled upon the term Use-After-Free, often shortened as UAF. On paper, it sounds pretty harmless — the program "uses" memory that's been "freed." But in reality? It's like your program is sleepwalking off a cliff. And attackers love it.
Understanding UAF Through a Real-World Example
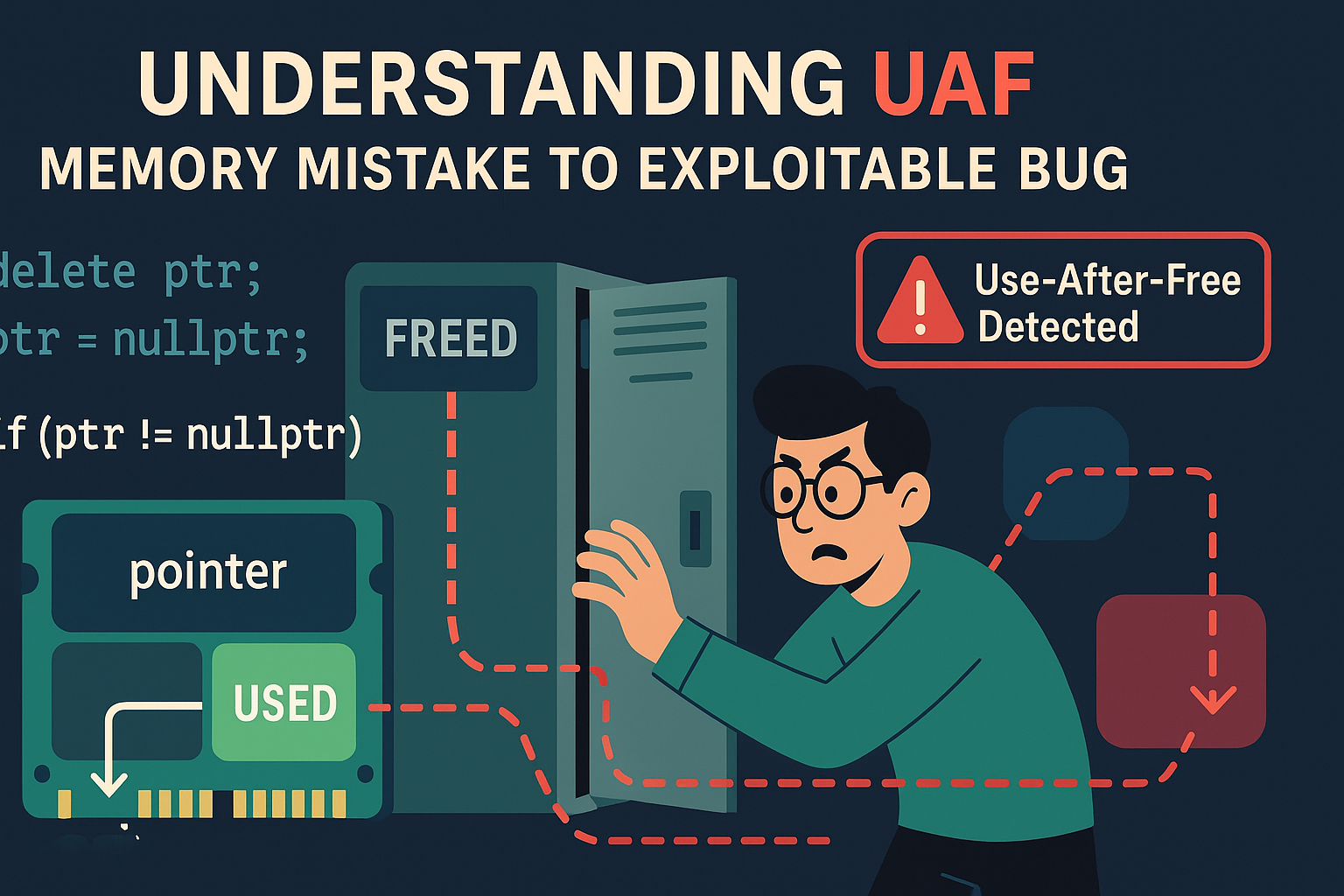
Meet Granth and His School Locker
Granth has a locker at school. Every day, he puts his lunchbox inside it. One day, he decides he doesn't need it anymore — so he clears the locker and tells the teacher, "I'm done with it."
The teacher reassigns the locker to another student, who puts their stuff in there.
But later that day, Granth forgets. He walks back to his old locker, opens it, and reaches inside expecting his lunch. But it's not his stuff anymore. It could be someone else's books, snacks, or maybe even a prank!
That's Use-After-Free in a nutshell.
Translating That to Code
In programming terms:
- Your program allocates memory for an object (like giving Granth a locker)
- Later, it frees that memory because it's no longer needed
- But then, for some reason, it tries to use that memory again — assuming it's still valid
Why It's a Big Deal in Exploit Development 🔥
So how does this innocent mistake turn into a full-blown security threat?
Because once memory is freed, it's up for grabs. And attackers know that. They can:
- Carefully spray the heap with controlled data
- Time their inputs to reallocate the freed memory with their malicious payload
- Then trick the program into using that old pointer, which now points to attacker code
Done right, this allows attackers to hijack the program's behavior — and in many cases, execute arbitrary code.
Real-World Examples
1. CVE-2014-1776 – Internet Explorer Zero-Day
This was a classic UAF vulnerability in Internet Explorer's handling of DOM objects. The browser would reference memory for a deleted object — allowing attackers to craft a malicious webpage that led to remote code execution.
It was bad enough that Microsoft had to issue an emergency patch, and it was known to be exploited by targeted attacks even before the patch was available.
2. CVE-2021-21166 – Chrome Audio Component
Even modern browsers like Google Chrome aren't immune. In 2021, a high-severity UAF bug was discovered in Chrome's audio component. If triggered correctly, it could allow attackers to break out of the sandbox or execute code within the browser process.
That same year, Google patched more than five different UAF vulnerabilities, showing how common (and dangerous) they still are.
How Can Developers Prevent UAF?
Developer Best Practices
Always null out pointers after freeing memory. This is simple but effective. Trying to use a null pointer will immediately crash (fail-fast), making it easier to debug.
Example (In C++):
#include
int main() {
int* ptr = new int(42);
std::cout << "Value: " << *ptr << std::endl;
delete ptr;
ptr = nullptr; // ✅ Null out pointer
// Later in the code...
if (ptr != nullptr) {
std::cout << *ptr << std::endl; // Won't be executed
} else {
std::cout << "Pointer is null, not using it!" << std::endl;
}
return 0;
} Use Smart Pointers
Avoid raw pointers when possible. In C++, for example, prefer std::unique_ptr or std::shared_ptr. These smart pointers automatically handle cleanup and avoid dangling pointers.
Example (In C++):
#include
#include
void useSmartPointer() {
std::unique_ptr smartPtr = std::make_unique(100);
std::cout << "Smart Pointer Value: " << *smartPtr << std::endl;
// No need to delete; automatically freed when out of scope
} Use Memory-Safe Languages
While not always practical in low-level development, using languages like Rust or Go for non-performance-critical components helps eliminate entire classes of memory bugs.
Example (In Rust):
fn main() {
let v = vec![1, 2, 3]; // Memory is managed
println!("{}", v[0]); // Safe access
// v is automatically dropped at the end — no free() needed
}Runtime Tools
- AddressSanitizer (ASan): A lifesaver during development. It catches UAF and other memory issues before they go to production.
- Valgrind: Slower but extremely thorough. Great for finding sneaky memory leaks and misuse.
- Static analysis tools: Many modern IDEs can detect potential UAF risks via control flow analysis.
OS and Hardware Level Protection
- Memory tagging (MTE) on ARM architectures
- Control-flow integrity (CFI) on modern operating systems
- Pointer authentication (on Apple silicon) to make pointer tampering harder
Why You Should Care
You don't have to be writing C code for embedded systems to care about Use-After-Free. Here's why this matters even to web devs or app builders:
- The software you build might depend on native libraries
- Attackers love to chain bugs together — a UAF in a browser + a sandbox escape in a driver = total system takeover
- Learning how UAF works gives you a deeper understanding of how systems manage memory, how exploits work, and how to build safer software
Final Thoughts
Use-After-Free is one of those bugs that sneaks in when memory management slips. It's easy to miss, hard to find, and incredibly powerful in the wrong hands.
But it's also a perfect example of how tiny oversights in code can become huge security problems. From forgotten lockers to million-dollar exploits, UAF is a lesson in the value of clean, cautious programming — and the creativity of attackers who wait for you to slip up.
If you're just starting out in cybersecurity, this is one vulnerability that teaches you a lot — about programming, exploitation, and secure software design.