Binary patching is a powerful technique used in cybersecurity and reverse engineering that allows modification of compiled programs without access to their source code. This article explores what binary patching is, how it works, and its applications in both defensive and analytical contexts.
What is Binary Patching?
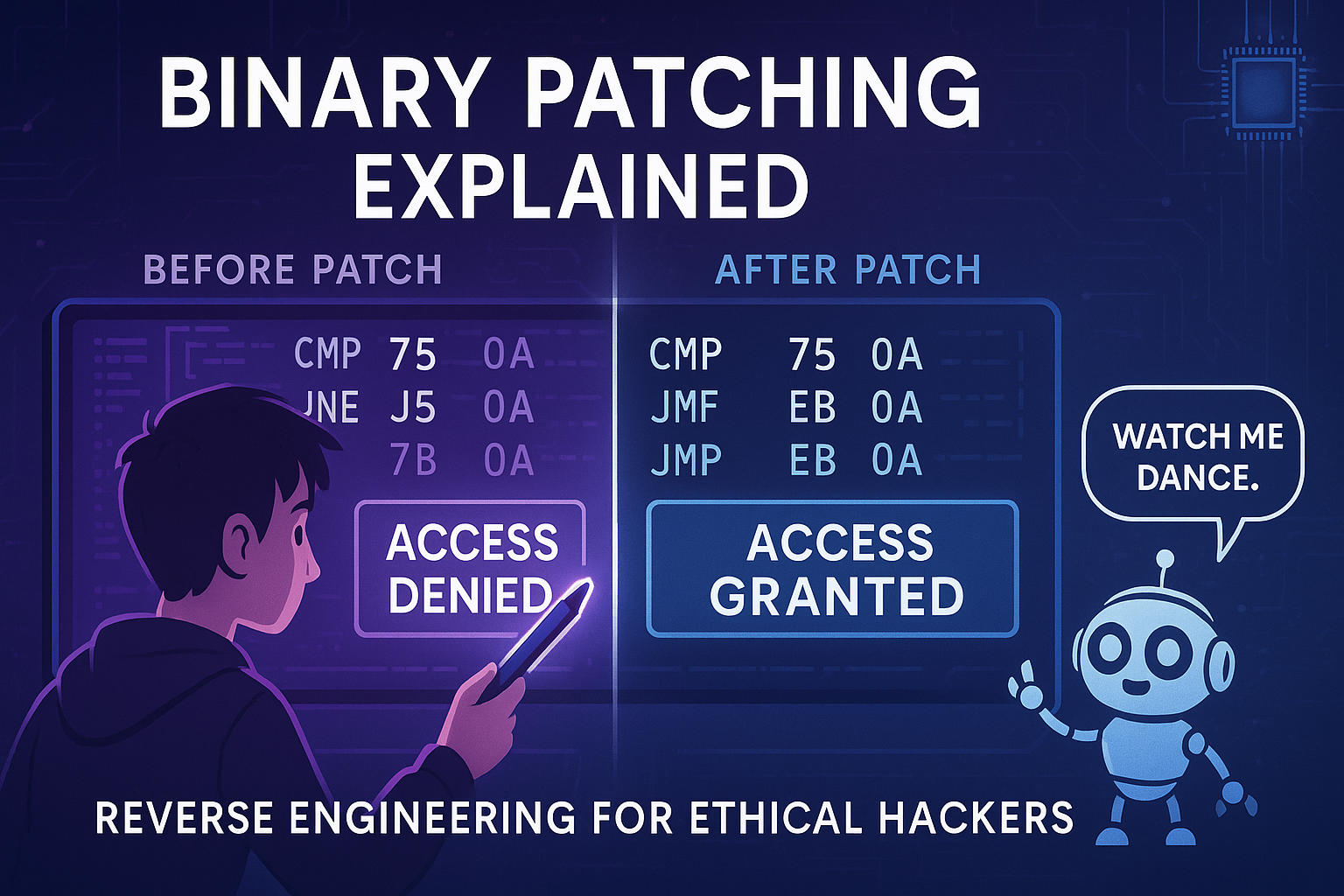
Binary patching is the act of modifying the machine code (compiled instructions) inside an executable program without needing access to its original source code. Think of it like correcting a typo in a printed book - you're making changes directly to the final product rather than editing the original manuscript.
Why Is It Called "Binary" Patching?
The term "binary" comes from working directly with the binary file (.exe, .dll, or Linux .elf), which is a compiled, low-level representation of the software that your computer can run. Instead of changing source code or debugging at runtime, you're making permanent changes to the actual bytes of the file stored on disk.
Understanding Binary Patching Through a Story
Meet Granth, a smart kid who loves robots. He has a toy robot that can walk and talk, but it only says "I don't dance." Granth wants it to dance, so he modifies the robot's memory chip to change its behavior - this is essentially what binary patching does with software!
How Binary Patching Works
1. Understanding the Target
Before making any changes, you must understand the behavior of the binary you want to patch. This involves:
- Running the binary to observe its behavior
- Noting input/output relationships
- Identifying specific functionality to modify
2. Disassembly Process
Using tools like IDA Pro, Ghidra, or Radare2, you convert the binary into assembly instructions that you can read and analyze. This helps you locate the exact code sections that need modification.
3. Making the Patch
Once you've identified what to change, you can modify the binary using:
- Hex editors for direct byte modification
- Disassemblers for instruction-level changes
- Specialized patching tools
Common Applications of Binary Patching
- Security research and vulnerability analysis
- Malware analysis and reverse engineering
- Legacy software maintenance
- Software debugging and testing
Important Facts About Binary Patching
1. Reversible Engineering
Binary patching is a form of controlled, reversible reverse engineering that requires deep understanding of how code behaves internally.
2. Memory-Only Patches
Some patches can be applied in memory without modifying the binary file, useful for malware analysis and testing.
3. Self-Verifying Binaries
Modern software often includes anti-tamper features that must be considered when patching:
- Integrity checks using various hash algorithms
- Runtime integrity scanning
- Virtualization-based obfuscation
4. Advanced Techniques
Binary patching isn't limited to just changing instructions. You can also modify:
- Import tables
- Configuration sections
- Resource sections
- Thread-local storage
Tools of the Trade
Common tools used in binary patching include:
- IDA Pro and Ghidra for disassembly
- HxD and other hex editors
- x64dbg and OllyDbg for debugging
- Radare2 for advanced analysis
Ethical Considerations and Disclaimer
Binary patching is a powerful technique that should be used responsibly. It's essential to:
- Obtain proper authorization before modifying software
- Use these skills for ethical purposes only
- Respect intellectual property rights
- Follow applicable laws and regulations
🚨 Disclaimer: This article is intended for educational and ethical research purposes only. Unauthorized modification of software may be illegal and unethical.